Disclaimer: This article focuses solely on key HIPAA compliance software testing aspects and does not encompass elements such as physical safeguards, including non-deployment of software on workstations with open screens. Additionally, it’s important to acknowledge that the strategy outlined may vary based on the specific requirements of the application and may not be universally applicable to all applications.
Emphasizing HIPAA-compliant software testing is crucial. Neglecting to test healthcare software with a focus on HIPAA compliance can result in data leaks and unauthorized usage. Furthermore, it may incur severe penalties from the US Department of Health and Human Services.
This underscores the importance of allocating sufficient time for your healthcare software development team to construct a HIPAA-compliant application, placing heightened emphasis on rigorous software testing.
The surge in data breach incidents within healthcare software organizations is a cause for serious concern, with notable cases like the Yuma Regional Medical Center ransomware attack in April 2022, exposing the data of more than 700,000 individuals. The escalating number of such breach occurrences is starkly illustrated in the accompanying graph.
As year-on-year statistics raise concerns, medical organizations are increasingly embracing software equipped with robust data protection measures to store and transmit medical data securely. Committed to fulfilling HIPAA compliance requirements, these organizations dedicate substantial efforts to guarantee the reliability and security of their healthcare software along with the Mobile App Security Best Practices.
As a healthcare software development company, Digiatto IT Services has effectively designed, tested, and implemented healthcare applications that engage various stakeholders, all without encountering a single instance of a security breach.
Why is building HIPAA-compliant software difficult?
A substantial volume of data requires safeguarding. Prior to establishing a framework for data protection, developers must possess a thorough comprehension of the components classified as sensitive information.
Lack of resources around HIPAA compliance
Inadequate resources for HIPAA compliance software testing present a hurdle. Developing software that genuinely adheres to HIPAA software testing standards necessitates the inclusion of lawyers, system architects, cybersecurity experts, and medical professionals in the team.
Multiple data access platforms
Securing all platforms within the healthcare system requires a cohesive security approach. However, a hospital’s infrastructure comprises both physical and digital user endpoints, data centers, servers, cloud resources, and more. To establish a unified security infrastructure, it is imperative to explore the development of Mobile Device Management (MDM) to safeguard sensitive data.
Lowered flexibility
Reduced flexibility can result from developing software with multiple security requirements. Healthcare organizations, nonetheless, require flexibility to effectively manage both patient and doctor experiences. This creates a scenario where developers must navigate the balance between maintaining flexibility and ensuring HIPAA compliance software testing without compromising the overall healthcare experience.
Need to reassess HIPAA implementation
Reassessing HIPAA software testing implementation is an ongoing necessity. The process of HIPAA compliance software testing extends beyond the deployment of the application. Given the dynamic nature of elements such as cybersecurity threats, evolving HIPAA software testing requirements, and the changing IT needs of healthcare organizations, ensuring continuous compliance requires regular audits and updates to documentation for your software.
Strategies and Areas for HIPAA software testing
To facilitate comprehension, HIPAA compliance software testing is commonly categorized into five key areas. Understanding these areas is crucial in addressing the question of how to verify that software adheres to HIPAA compliance standards.
User authentication
Typically, user authentication can be any of these – ownership-based like ID cards, like user ID/password, and biometric-based like fingerprint or face scan. Software testing on this front goes beyond ensuring a successful login path for each role and looks into –
Login failure due to –
- Empty user ID and password
- Invalid user ID and password
- Expired or blocked account
- Locked out account
- Login success post password change
In addition to this, it helps to create a standard structure of the test data, for example, <PatientFirstName><PatientLastName><TestName><Date><Time>. This will help in identifying users seamlessly.
Information disclosure
Information disclosure typically involves two categories: Role-based access and Patient allocation. In the former, users are organized into logical classes with designated access levels, while in the latter, supervisors assign patients to healthcare providers for specific period.
Designing test cases that explicitly outline permissions for viewing, modifying, adding, or deleting information not designated for specific users is essential. Furthermore, establishing a protocol where uninstalling the app results in the removal and deletion of all Electronic Protected Health Information (EPHI) from the system is crucial. Ensuring proper information disclosure should be a fundamental component of the HIPAA compliance software testing checklist.
- When examining the audit trails aspect of HIPAA software testing, consider the following factors:
- Each audit trail entry must include:
- Date and time of the action
- User ID or name of the user performing the action
- User access level
- Patient record ID on which the action occurred
- The location or system ID through which the action occurred
- Entries should adhere to the software’s security requirements, ensuring the audit trail is easily traceable for future investigations.
- Entries must not be deletable or removed from the audit trail.
- The audit trail should be configured for selective viewing by specific user accounts.
- All attempts to breach security should be actively monitored and logged in the audit trail.
- The audit trail itself must be encrypted to enhance data security.
Data transfers
Data transfers in the context of HIPAA compliance refer to the secure movement of electronic protected health information (ePHI) between various entities and locations within the healthcare ecosystem. This process involves the transmission of sensitive patient data between different systems, devices, or storage locations while ensuring the confidentiality, integrity, and availability of the information.
Key considerations during data transfers for HIPAA compliance include:
- Physical and Mobile Devices:
- Ensuring the secure exchange of data between physical devices (such as computers) and mobile devices where healthcare applications are installed.
- External Devices and Locations:
- Safeguarding data as it is transmitted to external devices, such as USB drives or external hard disks, and external locations, which could be offsite storage facilities or cloud servers.
- Data Movement to Offline Storage:
- Securing the data transfer process when moving patient information to offline storage locations, which may involve backup systems or archival storage.
Information on the correct data usage
- Data Usage Information:
The application should provide details on the correct usage of data before granting access.
Presentation methods may include a help page for EPHI-related operations or a training version of the app.
- Help Page for EPHI Operations:
Incorporate a help page within the application detailing proper procedures for operations involving Electronic Protected Health Information.
- Training Version of the App:
Develop a training version that enables users to familiarize themselves with the software’s functionality before accessing actual EPHI.
- Ensuring the Application of Principles:
Explore methods to ensure the integration of these critical areas in the healthcare application development process.
- Steps for Achieving and Upholding HIPAA Compliance:
Define a comprehensive strategy that includes Access Control, Sanity Testing, Roles Matrix creation, Test Cases, and Load Balancing.
- Upcoming Section:
The subsequent section will address the steps and strategies required to achieve and maintain HIPAA compliance in software testing within the healthcare application development process.
Steps to achieve and maintain HIPAA compliance in software testing
At Digiatto IT Services, our approach to building healthcare apps involves seamlessly integrating HIPAA software requirements into the entire development cycle, with a particular emphasis on testing. Here are some methodologies we employ to guarantee this integration.
1. Access Control:
Adhering to HIPAA compliance requirements mandates restricting user access to only the information necessary for a specific task. Achieving stringent access control involves implementing the following seven modes:
- A list of access controls granting user access to specific modules, applications, or areas.
- Assigning a unique name and number for the identification and tracking of each user within the system.
- User-driven access, requiring two-factor authentication for system entry.
- Role-driven access is contingent on users’ roles to determine access rights.
- Context-driven access, limiting access based on specific times, dates, networks, or information systems.
- Establishing a dedicated process for emergencies to collect critical Electronic Protected Health Information (ePHI).
2.Sanity Testing:
As part of our HIPAA software testing protocol, the initial step involves conducting a sanity test to identify potential defects in the app’s adherence to HIPAA compliance standards. This process includes scrutinizing the following areas:
Verification of High-Risk Roles or Relationships:
- Confirming that users with specific roles can easily authenticate.
- Ensuring users are appropriately granted view, modification, and deletion access or have no access to specific application component operations.
- Recording all performed actions in the audit trail.
Encryption Verification:
- Verifying encryption measures in critical areas such as audit trail entries and Electronic Protected Health Information (EPHI) stored in the database.
3.Roles Matrix:
In the scenario where the application employs role-based access, it becomes crucial to delineate the various roles within the system and define the extent of access they possess in the application. This undertaking is commonly initiated by engaging in discussions with clients who provide insights into risk levels based on factors such as information disclosure, frequency of usage, the likelihood of errors, and the impact of potential errors.
4. Test Cases:
As the third step in HIPAA compliance software testing, we undertake the creation of meticulous test cases wherein user interactions are meticulously deconstructed into action and result levels.
5.Load Balancing:
In any healthcare organization, failover or load balancing strategies are pivotal, as the loss of a patient’s data could significantly disrupt their life. These plans are essential for validating the software’s ability to sustain day-to-day operations while concurrently creating backups for seamless workflow continuity. They play a crucial role in assessing whether the software can efficiently allocate resources when necessary and promptly identify situations of urgency or need.
Process we follow for HIPAA compliance testing
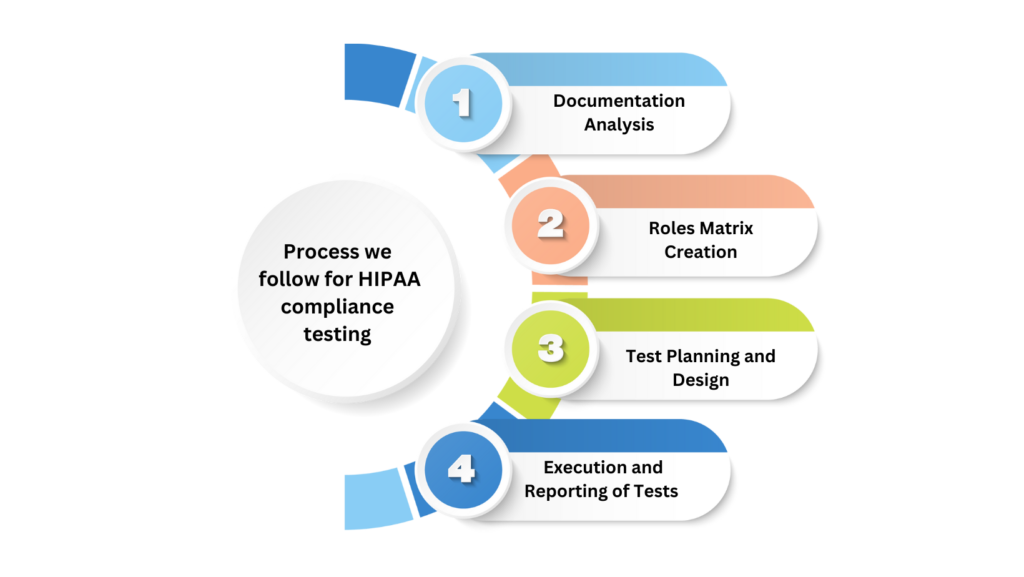
Testing a health app for HIPAA compliance requires a distinct approach compared to conventional app testing methodologies. Here is the methodology we employ to ensure thorough testing of your application.
1. Documentation Analysis:
Our team of Quality Assurance specialists thoroughly examines the software documentation, encompassing both functional and non-functional requirements. This process is conducted to compile a checklist of the necessary technical safeguards required for your software. Subsequently, we formulate a comprehensive HIPAA compliance testing plan based on these findings.
2. Roles Matrix Creation:
We construct a roles matrix chart aimed at identifying the existing user roles and assessing the associated risk levels concerning various operations such as viewing, adding, deleting, and modifying Electronic Protected Health Information (ePHI).
3.Test Planning and Design:
Initiating the process involves delineating the necessary testing events for assessing software compliance with HIPAA technical safeguards, including vulnerability assessment, functional testing, and penetration testing.
Subsequently, we outline the composition of the testing group, determining the number of test engineers, automation experts, security testers, and other relevant roles.
Following this, we construct pertinent test scenarios and test cases, strategically outlining the testing approach.
We then determine the proportion of test automation, crafting scripts and configuring relevant test automation tools.
Ultimately, we prepare the mandatory test environment and generate requisite test data to facilitate a thorough testing process.
4.Execution and Reporting of Tests:
- Conducting both manual and automated tests aligning with predefined test scenarios.
- Generate comprehensive reports outlining identified gaps in HIPAA compliance.
- Conclude the testing process by proposing requisite remediation measures.
Having explored various aspects of testing an application to meet all HIPAA requirements, along with detailing our testing process, we will now delve into the associated costs as we conclude this article.
The Cost of HIPAA Compliance Testing
The individual cost of HIPAA testing hinges on various factors:
- The type and complexity of healthcare software.
- The number of distinct user roles.
- The applicable HIPAA technical testing safeguards.
- The required testing types.
- The effort needed for test automation.
- The complexity and quantity of test cases.
- The chosen software testing sourcing model (in-house or outsourcing).
- The costs associated with security testing tools.
By adhering to these five HIPAA software testing practices and following our established process for HIPAA compliance testing, we ensure the development of a compliance-ready application poised to make a transformative impact on the digital landscape while maintaining impervious security at all times. This achievement is realized by anchoring our design, development, and maintenance efforts on the foundation of the HIPAA compliance software checklist.
If you seek assistance in building or testing a HIPAA-ready application, don’t hesitate to reach out to us today.


